| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
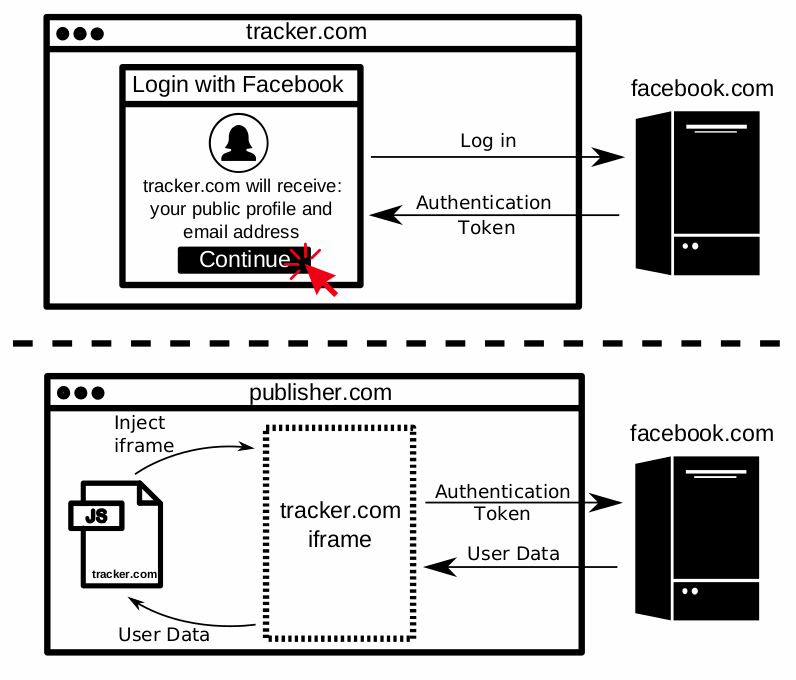
美国普林斯顿大学的研究人员发现在434个拥有可用Facebook登录功能的网站,可第三方服务的JavaScript代码窃取用户登录凭据。数据收集的第一个场景是JavaScript代码能够拦截这些用户数据。第二个数据收集场景是通过隐藏的iframe进行窃取。 [出自:jiwo.org]
JavaScript libraries from various advertising and analytics services are siphoning user data from web pages where the "Login with Facebook" feature is being used.
Academics from Princeton University discovered that 434 of the top 1 million sites are loading JavaScript code from third-party services that are dipping into "Login with Facebook" data.
Researchers believe that most of the 434 services are likely unaware that this is happening on their sites.
The research team says that the data collection usually occurs in two different ways. The first case is on sites that use a "Login with Facebook" feature to authenticate users.
When a user wants to log into his account, the "Login with Facebook" feature makes a request to Facebook servers, which respond back with the Facebook account data that a user has allowed that specific site to access.
Third-party JavaScript code that loads on the login page is capable of intercepting this data and extracting user details.
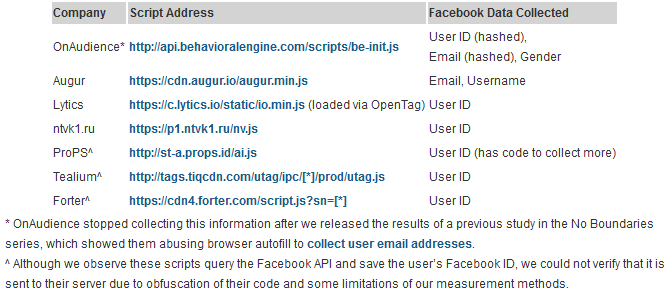
Princeton researchers say they've identified seven analytics/user-tracking services engaging in such practices [table below].
But while some of these tracking and analytics services collected what appeared to be benign data —in the form of the app-specific user ID— the Princeton team says this app user ID can be converted back to a Facebook ID and later used to obtain more information about a site's visitor.
The second data collection scenario is a bit more complex than the first. The idea is if a site uses a "Login with Facebook" system that lets users log in using Facebook credentials, rogue third-party analytics services can embed a hidden iframe on other sites to trick users' browsers into authenticating using their Facebook login.
Just like in the first scenario, the third-party tracking script can then intercept the Facebook login data and extract the user's info.
According to the Princeton team, they only found this second scenario used only once with the Bandsintown service, which fixed the issue once reported by the Princeton team. This prevented any future attacks that would have tried to abuse Bandsintown's "Login with Facebook" feature to harvest user details.
"This unintended exposure of Facebook data to third parties is not due to a bug in Facebook’s Login feature," Princeton researchers explained. "Rather, it is due to the lack of security boundaries between the first-party and third-party scripts in today’s web."
"Still, there are steps Facebook and other social login providers can take to prevent abuse: API use can be audited to review how, where, and which parties are accessing social login data. Facebook could also disallow the lookup of profile picture and global Facebook IDs by app-scoped user IDs. It might also be the right time to make Anonymous Login with Facebook available following its announcement four years ago," researchers said.
Article was updated on April 19, 03:25 ET to remove the names of three web services that loaded scripts from services known to collect Login with Facebook user data. The Princeton team says these three sites were given as examples and they did not observe data collection on these sites.
Data collection scenario #1
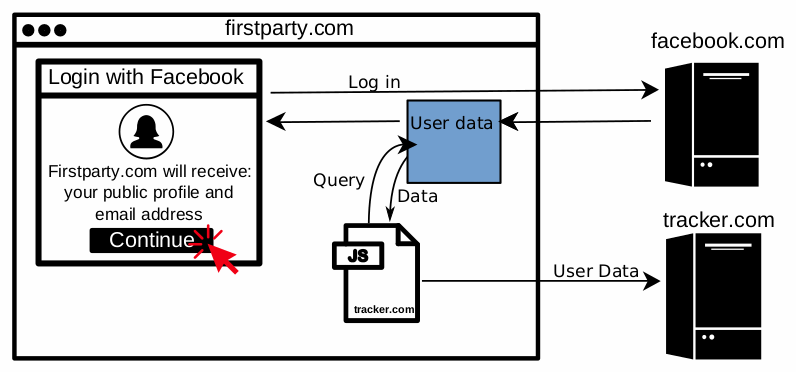
Data collection scenario #2