| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
Open Sourcing JA3

SSL/TLS Client Fingerprinting for Malware Detection
开源 JA3[出自:jiwo.org]
用于恶意软件检测的 SSL/TLS 客户端指纹识别
A JA3 hash represents the fingerprint of an SSL/TLS client application as detected via a network sensor or device, such as Bro or Suricata. This allows for simple and effective detection of client applications such as Chrome running on OSX (JA3=94c485bca29d5392be53f2b8cf7f4304) or the Dyre malware family running on Windows (JA3=b386946a5a44d1ddcc843bc75336dfce) or Metasploit’s Meterpreter running on Linux (JA3=5d65ea3fb1d4aa7d826733d2f2cbbb1d). JA3 allows us to detect these applications, malware families, and pen testing tools, regardless of their destination, Command and Control (C2) IPs, or SSL certificates.
JA3 哈希表示通过网络传感器或设备(例如 Bro 或 Suricata)检测到的 SSL/TLS 客户端应用程序的指纹。 这允许简单有效地检测客户端应用程序,例如在 OSX 上运行的 Chrome (JA3=94c485bca29d5392be53f2b8cf7f4304) 或在 Windows 上运行的 Dyre 恶意软件系列 (JA3=b386946a5a44d1ddcc843bc75336Metadfloit'ad2f37d37d360dfcead37d360dfcead36d37d36dfloit’ad35cd37d37d37d36dfloit'ad35d37d37d36dfloit'ad35cd2f36)。 JA3 允许我们检测这些应用程序、恶意软件系列和渗透测试工具,而不管它们的目的地、命令和控制 (C2) IP 或 SSL 证书如何。
JA3 has been open sourced and is available here: GitHub - salesforce/ja3: JA3 is a standard for creating SSL client fingerprints in an easy to produce and shareable way.
JA3 已开源并可在此处获得:GitHub - salesforce/ja3:JA3 是一种以易于生产和共享的方式创建 SSL 客户端指纹的标准。
JA3 was created by:
- John B. Althouse
- Jeff Atkinson
- Josh Atkins
How it works
TLS and its predecessor, SSL, I will refer to both as “SSL” for simplicity, are used to encrypt communication for both common applications, to keep your data secure, and malware, so it can hide in the noise. To initiate a SSL session, a client will send a SSL Client Hello packet following the TCP 3-way handshake. This packet and the way in which it is generated is dependent on packages and methods used when building the client application. The server, if accepting SSL connections, will respond with a SSL Server Hello packet, thus continuing the cryptographic negotiation. Because SSL negotiations are transmitted in the clear, it’s possible to fingerprint and identify client applications using the details in the SSL Client Hello packet.
TLS 及其前身 SSL,为了简单起见,我将两者都称为“SSL”,用于加密常见应用程序的通信,以确保您的数据安全和恶意软件,因此它可以隐藏在噪音中。 要启动 SSL 会话,客户端将在 TCP 3 次握手后发送 SSL 客户端 Hello 数据包。 此数据包及其生成方式取决于构建客户端应用程序时使用的包和方法。 服务器,如果接受 SSL 连接,将使用 SSL Server Hello 数据包进行响应,从而继续加密协商。 由于 SSL 协商以明文形式传输,因此可以使用 SSL Client Hello 数据包中的详细信息对客户端应用程序进行指纹识别和识别。
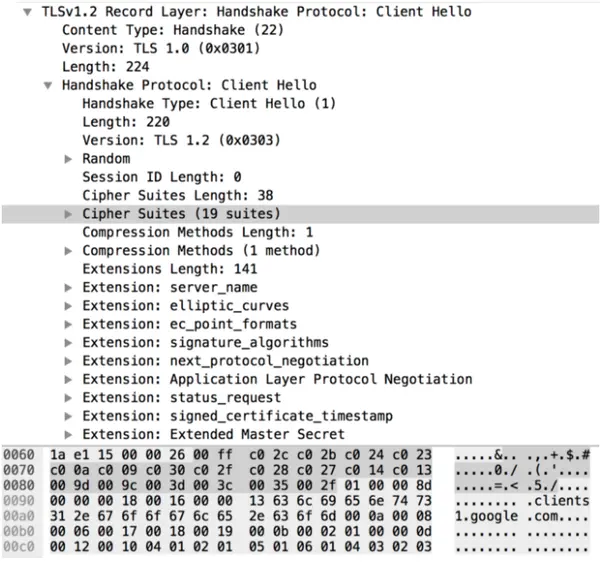
Using details within the SSL Client Hello packet to help identify a client application is not a new concept. Blog posts such as this date back to 2009. In 2015, Lee Brotherston published the most research on the topic and released FingerprinTLS, a stand-alone tool for the job which got a lot of people excited, myself included.
使用 SSL Client Hello 数据包中的详细信息来帮助识别客户端应用程序并不是一个新概念。 诸如此类的博客文章可以追溯到 2009 年。 2015 年,Lee Brotherston 发表了最多的关于该主题的研究,并发布了 FingerprinTLS,这是一个让很多人兴奋的工作的独立工具,包括我自己。
It was then that we set out to create a SSL Fingerprinting solution that would work on existing tools, whether it’s a network security monitoring tool or a load balancer. The fingerprints needed to be unique to the client application and agnostic to it’s destination. We also wanted them to be easy to create and share, meaning they needed to be easily consumed by others and their tools, which could be vastly different from our own. This means that simplicity is key, the more simple the process and output, the more likely it will work with existing technologies.
就在那时,我们着手创建一个 SSL 指纹解决方案,该解决方案适用于现有工具,无论是网络安全监控工具还是负载均衡器。 指纹需要对客户端应用程序是唯一的,并且与其目的地无关。 我们还希望它们易于创建和共享,这意味着它们需要易于被其他人和他们的工具使用,这可能与我们自己的大不相同。 这意味着简单性是关键,过程和输出越简单,它就越有可能与现有技术一起工作。
A common initial thought process is to just hash the entire packet, easy. But this doesn’t work as there’s a random string within the packet as well as certain SSL extensions which can hold destination specific information like the “Server_Name” extension which holds the destination domain. After some trial and tribulation, we finalized on a process that ticked all the boxes and is simple enough that it should be easy to add to existing tools.
一个常见的初始思维过程是简单地散列整个数据包。 但这不起作用,因为数据包中有一个随机字符串以及某些可以保存目标特定信息的 SSL 扩展,例如保存目标域的“Server_Name”扩展。 经过一些试验和磨难,我们最终确定了一个过程,该过程符合所有条件,并且足够简单,应该很容易添加到现有工具中。
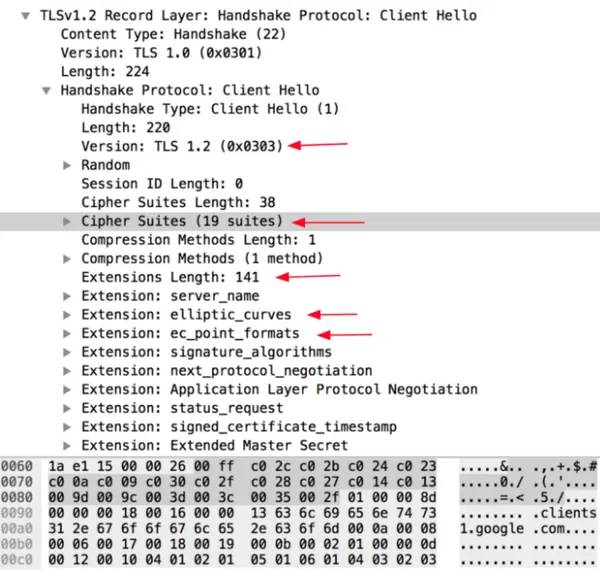
JA3 gathers the decimal values of the bytes for the following fields; SSL Version, Accepted Ciphers, List of Extensions, Elliptic Curves, and Elliptic Curve Formats. It then concatenates those values together in order, using a “,” to delimit each field and a “-” to delimit each value in each field.
JA3 为以下字段收集字节的十进制值; SSL 版本、接受的密码、扩展列表、椭圆曲线和椭圆曲线格式。 然后按顺序将这些值连接在一起,使用“,”分隔每个字段,使用“-”分隔每个字段中的每个值。
The field order is as follows:
SSLVersion,Ciphers,Extensions,EllipticCurves,EllipticCurvePointFormats
Example:
769,47–53–5–10–49161–49162–49171–49172–50–56–19–4,0–10–11,23–24–25,0
If there are no SSL Extensions in the Client Hello, the fields are left empty.
如果 Client Hello 中没有 SSL 扩展,则这些字段留空。
Example:
769,4–5–10–9–100–98–3–6–19–18–99,,,
These strings are then MD5 hashed to produce an easily consumable and shareable 32 character fingerprint. This is the JA3 SSL Client Fingerprint.
然后对这些字符串进行 MD5 散列以生成易于使用和共享的 32 个字符指纹。 这是 JA3 SSL 客户端指纹。
769,47–53–5–10–49161–49162–49171–49172–50–56–19–4,0–10–11,23–24–25,0
→ ada70206e40642a3e4461f35503241d5
769,4–5–10–9–100–98–3–6–19–18–99,,,
→ de350869b8c85de67a350c8d186f11e6
We also needed to introduce some code to account for Google’s GREASE (Generate Random Extensions And Sustain Extensibility) as described here. Google uses this as a mechanism to prevent extensibility failures in the TLS ecosystem. JA3 ignores these values completely to ensure that programs utilizing GREASE can still be identified with a single JA3 hash.
我们还需要引入一些代码来解释谷歌的 GREASE(生成随机扩展和维持可扩展性),如此处所述。 Google 将此用作防止 TLS 生态系统中的可扩展性失败的机制。 JA3 完全忽略这些值以确保使用 GREASE 的程序仍然可以用单个 JA3 哈希识别。
Utilizing JA3
使用 JA3
This Bro script will add JA3 to every connection observed in ssl.log:
这个 Bro 脚本会将 JA3 添加到 ssl.log 中观察到的每个连接:
Build software better, together
This Python script will output JA3 details from pcaps:
这个 Python 脚本将从 pcaps 输出 JA3 详细信息:
ja3/python at master · salesforce/ja3
JA3 support has also been added to Moloch and Trisul NSM as of this writing.
在撰写本文时,还向 Moloch 和 Trisul NSM 添加了 JA3 支持。
Example Analysis
JA3 is currently running on the internal Fighting malware and botnets Sandnet. If you’re not familiar with Fighting malware and botnets, I highly recommend you take a look at their malware trackers and blacklists. Within the Sandnet we find a malware sample which has had no internal signatures match and no VirusTotal hits.
JA3 目前运行在内部 Fighting 恶意软件和僵尸网络 Sandnet 上。 如果您不熟悉对抗恶意软件和僵尸网络,我强烈建议您查看他们的恶意软件跟踪器和黑名单。 在 Sandnet 中,我们发现了一个恶意软件样本,它没有内部签名匹配,也没有 VirusTotal 命中。
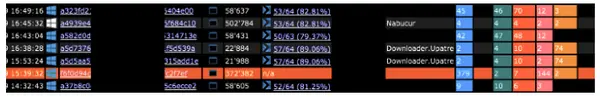
Diving into this example we can see the malware made several SSL connections outbound, all with the same JA3 fingerprint.
深入这个例子,我们可以看到恶意软件建立了多个 SSL 连接出站连接,所有连接都具有相同的 JA3 指纹。
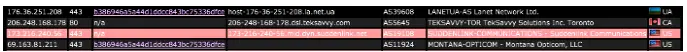
Pivoting on the JA3 fingerprint we can see that it was found in 112 other malware samples with most of them matching the Dyre malware family. We can now say with confidence this sample is related to Dyre so we add it to the blacklist.
以 JA3 指纹为中心,我们可以看到它在 112 个其他恶意软件样本中被发现,其中大多数与 Dyre 恶意软件系列相匹配。 我们现在可以自信地说这个样本与 Dyre 相关,因此我们将其添加到黑名单中。
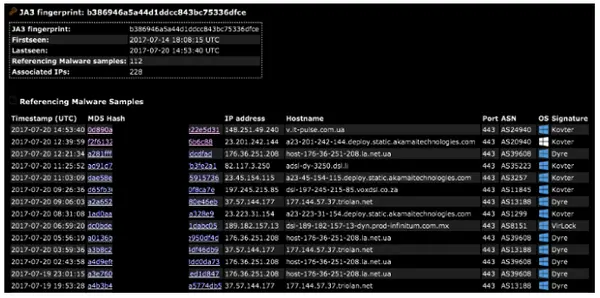
Traditionally one might turn the 228 associated IPs into low confidence IOCs. But with JA3, we can simply add one, single high confidence IOC to the blacklist. That’s because JA3 allows us to detect malware based on how it communicates rather than what it communicates to.
传统上,人们可能会将 228 个关联的 IP 变成低置信度的 IOC。 但是使用JA3,我们可以简单地将一个单一的高置信度IOC添加到黑名单中。 这是因为 JA3 允许我们根据恶意软件的通信方式而不是其通信对象来检测恶意软件。
Tor, as another example, could be detected by monitoring the thousands of exit nodes throughout the internet. But one can also detect the standard Tor client simply with JA3=e7d705a3286e19ea42f587b344ee6865.
作为另一个例子,Tor 可以通过监控整个互联网的数千个出口节点来检测。 但是也可以简单地使用 JA3=e7d705a3286e19ea42f587b344ee6865 检测标准 Tor 客户端。
Conclusion
JA3 is a much more effective way to detect malicious activity over SSL than IP or domain based IOCs. Since JA3 detects the client application, it doesn’t matter if malware uses DGA (Domain Generation Algorithms), or different IPs for each C2 host, or even if the malware uses Twitter for C2, JA3 can detect the malware itself based on how it communicates rather than what it communicates to.
与基于 IP 或域的 IOC 相比,JA3 是一种更有效的检测 SSL 恶意活动的方法。 由于 JA3 检测客户端应用程序,因此无论恶意软件是否使用 DGA(域生成算法)或每个 C2 主机的不同 IP,或者即使恶意软件使用 Twitter 进行 C2,JA3 都可以根据它如何检测恶意软件本身 沟通而不是它沟通的对象。
JA3 is also an excellent detection mechanism in locked-down environments where only a few specific applications are allowed to be installed. In these types of environments it is trivial to build a whitelist of expected applications and then alert on any other communication.
在只允许安装少数特定应用程序的锁定环境中,JA3 也是一种出色的检测机制。 在这些类型的环境中,构建预期应用程序的白名单然后对任何其他通信发出警报是微不足道的。
Certainly, more analysis needs to be done with JA3, on what it can detect as well as other things it could be used for. We’ve open sourced JA3 and are looking forward to feedback from the community. You can find JA3 here: https://github.com/salesforce/ja3 and can contact me on twitter @4A4133 or over email. Let me know what you find and if you have any feature requests.
当然,需要对 JA3 进行更多分析,分析它可以检测到的内容以及它可以用于的其他内容。 我们已经开源 JA3,期待社区的反馈。 您可以在此处找到 JA3:https://github.com/salesforce/ja3,并且可以通过 Twitter @4A4133 或通过电子邮件与我联系。 如果您有任何功能要求,请告诉我您找到了什么。

