| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
安全研究人员发现一个ElasticSearch服务器数据在网络上暴露出来,其托管着有关1,133个国家橄榄球联盟(NFL)球员和代理人信息数据。
Security researchers, and what appears to be at least one hacker, have found an ElasticSearch server left exposed online that was hosting information about 1,133 National Football League (NFL) players and agents.
According to the Kromtech Security Center, the security company that found the exposed data, the ElasticSearch server was being used to store data collected from a number of NFL domains.
The data included web analytics, but also information on NFL players. It is unknown if the data belongs to current, or past players.
The source of the data appears to be Orchard Audit, a user tracking module for Orchard, an ASP.NET CMS. According to W3Techs, the NFLPA website uses the Orchard CMS.
Kromtech Chief Communication Officer Bob Diachenko says the ElasticSearch database where the CMS module was sending data was left exposed online, and anyone could access the server without authentication.
After analyzing the server, researchers found the following data:
The most sensitive information was related to NFL players and agents. Kromtech says it found emails, mobile phone numbers, home addresses, and IP addresses used to sign-in and access the NFLPA dashboard.
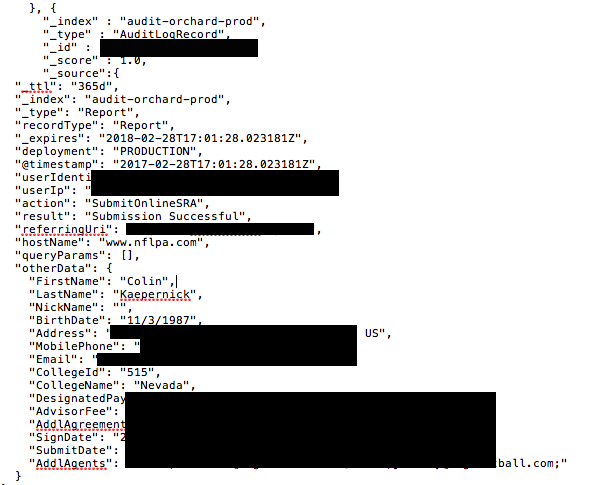
Among the exposed data was also the personal details of former 49ers quarterback Colin Kaepernick. Kaepernick has previously told the media that he received numerous death threats following his decision to protest by taking a knee during the national anthem before NFL games last year. Similar protests have continued this year, even if Kaepernick has not found a new team for the current season, but he's still considered the face of the movement.
Kromtech said it informed the NFLPA about the exposed server and the Association secured it shortly after their email but did not respond to researchers.
In most leaks of this kind, the data is rarely accessed by another party. For this case, Diachenko says that at least one hacker has found the data.
According to Diachenko, somebody accessed the NFLPA ElasticSearch server on February 3, 2017, and left the following message inside the database.
The message was saved inside a table named "pleasereadthis please_read warning." Despite the ominous warning, there was no public data leak.
Diachenko told Bleeping Computer the message "seemed that it was left by a script."
The expert is referencing the ransom attacks on exposed database servers that have taken place in the first half of 2017. Attacks targeted MongoDB, ElasticSearch, Hadoop, CouchDB, Cassandra, and MySQLservers.
Over 4,600 ElasticSearch servers were targeted and ransomed in January and February, and this appears to be one of them.
Earlier this year, Diachenko and his Kromtech team also discovered over 4,000 ElasticSearch servershosting PoS malware files.
ElasticSearch server left exposed online without a password
⬩ Records from 2017 - “audit-orchard-prod” total -406,284 : creation date: 2017-02-03
⬩ Emails (agent + player) - 1,262 records
⬩ 75 @nflpa.com emails
⬩ Agents/managers IP addresses
⬩ Players physical address
⬩ Players mobile phone numbers
⬩ Designated Payee number codes
⬩ Advisor fee percentages
⬩ 68 Urls or pages within the domain
⬩ 22,974 Hashes (widely used in computer software for rapid data lookup)
⬩ 26,271 IP Addresses -related to signed-in users and login location
Sensitive data on NFL players and agents included as well
Hacker left ransom note on NFLPA's server
{
"pleasereadthis":{
"aliases":{
},
"mappings":{
},
"settings":{
"index":{
"creation_date":"1486167641590",
"uuid":"KGijVP-WT4unr85SWlm-sw",
"notice":"SEND 0.1 BITCOIN TO THIS WALLET: 1EomYAqKiyrH4oRAV4AVHoMDGkn9MkFFxN IF YOU WANT RECOVER YOUR DATABASE! SEND TO THIS EMAIL YOUR SERVER IP AFTER SENDING THE BITCOINS e145t1c@sigaint.org IF PAYMENT IS NOT MADE WITHIN 120 HOURS WE WILL LEAK THE DATABASE TO PUBLIC. HOW TO BUY BITCOIN: https://en.bitcoin.it/wiki/Buying_Bitcoins_(the_newbie_version)",
"number_of_replicas":"1",
"number_of_shards":"5",
"version":{
"created":"1050199"
}
}
},
"warmers":{
}
}
}

